Vulnerability Management
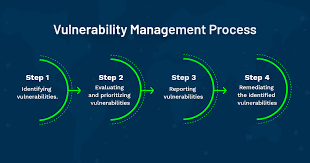
Vulnerability management is the process of identifying, evaluating, prioritize, and respond to software issues, week points and misconfigurations that could be exploited by attackers, lead to inadvertent release of sensitive data, or disrupt business operations.
Vulnerability Management vs. Vulnerability Assessment
Only the initial stage of vulnerability management is a vulnerability assessment.
The following are the primary categories of vulnerabilities:
- Network vulnerabilities: Malicious actors use weaknesses in software, hardware or operational processes, such as outdated firewall rules and improperly configured Wi-Fi access points, to get access to the network.
- Operating system vulnerabilities: Malicious actors use these bugs in operating system software to get access the other components of an asset or network to cause damage.
- Configuration vulnerabilities: To target networks and devices, cybercriminals use these vulnerabilities that result from incomplete installations, sloppy system updates, and default deployments.
- Application vulnerabilities: Cybercriminals use these defects to undermine the security of an application, putting everyone using it at risk.






